Choosing an Integration Strategy
Review the Different Options for Sending Device Data to a 3rd Party Platform.
Table of Contents
What is Integration?
Device Manager is simply a management and configuration platform, your customers will not be able to use their devices to track shipments, prevent theft, or monitor usage without on-sending device data into another (downstream) system. As a result, Device Manager has been built to easily transmit data in a variety of common formats. With the exception of Digital Matter's own Telematics Guru platform, your organization will always be responsible for the connection and maintenance of any software downstream of Device Manager.
Billing for Connectors
All Device Manager facilitated integration options carry a per-device charge. See Device Manager Billing for more information.
List of Integration Options
There are several options for integrating, which are outlined below.
| Option Name | Data Flow | What's Involved | Considerations |
|---|---|---|---|
| Telematics Guru and webhooks |
↓ Device ↓ Device Manager ↓ Telematics Guru 3rd party platform |
Digital Matter will set up the Telematics Guru partner account for you and send you an invite link along with user guides. | Effortless, good hybrid approach where end users would see benefits in TG and another highly specific application |
| Raw TCP payload via Device Manager |
↓ Device ↓ Device Manager 3rd party platform |
Create a Connector via the Device Manager UI. | High effort, commonly used format |
| JSON HTTPS payload via Device Manager |
↓ Device ↓ Device Manager 3rd party platform |
Create a Connector via the Device Manager UI. | Low barrier to entry, human-readable data. |
| JSON MQTT payload via Device Manager |
↓ Device ↓ Device Manager 3rd party platform |
Create a Connector via the Device Manager UI. | Human-readable data, secure connection protocol popular for IoT devices. |
| Device Gateway |
↓ Device ↓ Device Gateway 3rd party platform |
Obtain access to our container registry, self-host an instance of Device Gateway, obtain a database key, import device keys. |
Air-gapped solution created for government and security-conscious applications. No Digital Matter access. Contact Digital Matter support to learn more. |
| Raw TCP payload to 3rd party server ⚠️ |
↓ Device 3rd party platform |
Initially configure devices via Device Manager when provisioning. After picking up the loaded instructions, the device changes to communicate with a 3rd party server. For details see Setting up Direct to 3rd Party Server messaging on devices. |
Maximum effort, no ongoing cost charged by Digital Matter, limited ability for Digital Matter to offer support and assistance due to the lack of Device Manager diagnostics. Lack of aiding data will reduce GNSS accuracy and battery life. ⚠️Not Recommended⚠️
|
Integration for Edge Devices
Our Edge, Core and Fusion range od devices make use of our Location Engine to resolve positions. The only available integration option for these devices is an HTTPS JSON integration. Contact support for details
Message Format
Regardless of which strategy you choose, you will need to understand the data formats available:
- Raw TCP Connector: Device Manager forwards data in the device's native format - raw binary data over a TCP socket. The raw TCP protocol is described in documentation from Digital Matter. Contact our support team for these integration documents.
- JSON HTTPS Connector: Device Manager translates the raw data from the device into JSON and uses an HTTPS POST to deliver the records to an endpoint. This can be simpler to interpret but is less performant for large numbers of devices.
- JSON MQTT Connector: Device Manager translates the raw data from the device into JSON and uses an publishes via MQTT to a broker of your choice.
Integration Documents
Digital Matter provides documentation and support resources for device integration. These are available under NDA, and are sometimes subject to a support package fee. Contact our support team for integration documents containing the specifics of payload information and structure.
For information about which specific documentation you will require, please review the recommendations under your chosen integration option below.
1. Telematics Guru and Webhooks
System Design
While nominally representing a full-featured IoT software platform in its own right, Telematics Guru (TG) offers some interesting integration options for 3rd party platforms. Your end users may choose TG for traditional telematics software features (mapping, geo fences, etc) but also need to push selected events into another system. For this, Telematics Guru can use webhooks to curate selected events onwards to another system.
Examples of scenarios where using webhooks would be an ideal choice:
- Integration into hiring/maintenance software. TG is used for tracking, geofencing, driver behaviour monitoring, alerting etc - but the run hours and odometer readings are pushed from TG into the other system periodically (like at the end of each trip)
- Email integration into a ticket management system - to action alerts.
The diagram below shows the flow of data. Data is sent through the usual mechanism via Device Manager to TG - and then Webhooks can be set up to send information to a 3rd party platform.

Given the device/asset will be active in Telematics Guru, this implies the TG asset fee will be charged, for use of TG. There is no additional fee for the webhook functionality, and any number can be configured.
Setup in Device Manager
Your devices should already have a TG connector set by Digital Matter administrators. If this is not the case, please contact support.
Integration Documents Required:
None. For more details on webhooks see Alert Notifications through WebHooks.
2. Device Manager with TCP connector
System Design
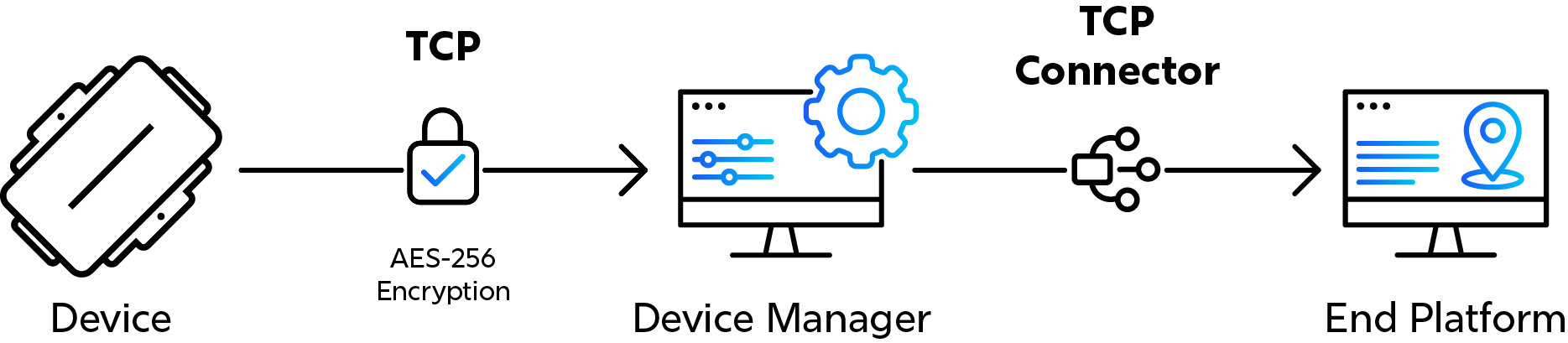
In this model, devices first connect to Device Manager, which then takes charge of sending any device data onwards through a Connector.
-
Device data - telemetry/sensor data is sent first to Device Manager, and then forwarded with a Connector. The connector specifies the endpoint's location (URL:port). Data is sent in the device's native protocol, which is a raw TCP protocol. A TCP socket is opened per device connection.
- Device management - all of the device management and debugging features are available through the Device Manager web user interface.
Many large-scale integrations favour the raw TCP connector over the HTTPS connector for its widespread use throughout the industry.
Setup in Device Manager
Create a Connector in Device Manager, then Set the Connector on your device(s) - to send data from these devices to your endpoint.
Integration Documents Required:
For Raw TCP integration you will require these 4 documents:
-
DMT Device Integration - Flexi Record: this explains the various messages sent by the device, and the expected responses from the end server. The protocol uploads data in "Flexi Messages". These are variable length messages, where the payload made up of a number of data records
-
DMT Data Fields: within the data records, there are a number of fields. The data within the fields is explained by this document. Fields are of variable length, and their type and length is described by a field header (Field ID + Field Length).
-
DMT Log Reasons: The data records contain a log reason in the header. This document describes the various log reasons, which is the reason why the record was generated (i.e. movement, heading change, input change)
- Integration Guide: Provides some context to the data fields and tips on the integration process.
3. Device Manager with the JSON HTTP/HTTPS connector
System Design
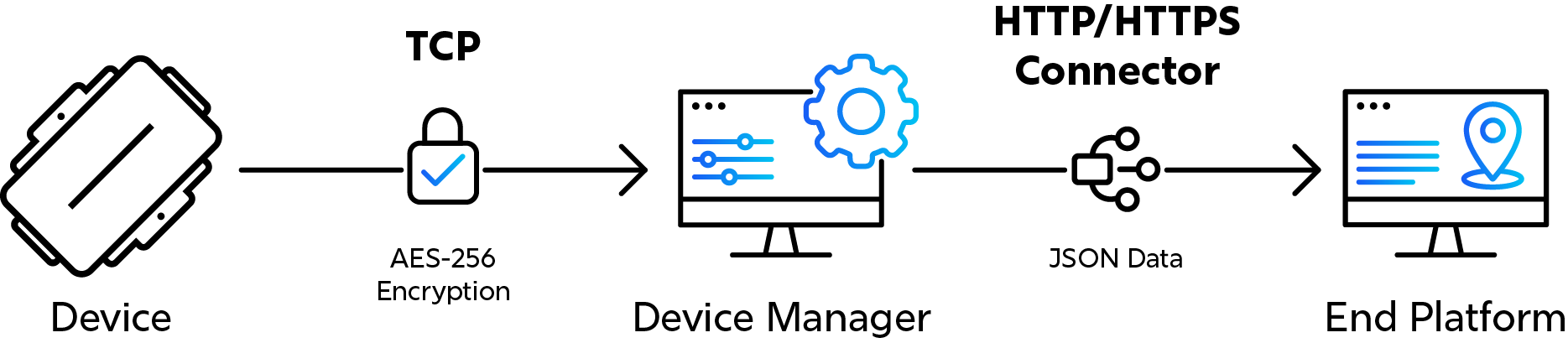
In this model, devices first connect to Device Manager, which then takes charge of sending any device data onwards through a Connector.
-
Device data: data is sent to Device Manager, and forwarded with a connector. Device Manager translates the device's native protocol into a JSON format and these records are sent to an endpoint over an HTTP/S POST. The connector specifies the endpoint location, and optionally: SSL (HTTPS); basic authentication; and some custom header options.
- Device management: all of the device management and debugging features are available through the Device Manager web user interface.
Device Manager cannot be bypassed in this setup, as the JSON HTTPS conversion happens on Device Manager. The HTTP/JSON connector is considered marginally less performant than the TCP connector.
Many users prefer this option over the TCP option, as messages do not need to be parsed out of the TCP stream of bytes - which can be a learning curve for developers not used to writing TCP listeners. In contrast, many developers will be used to working with JSON - so it can be faster to integrate devices using this method.
To Get Started
Create a Connector in Device Manager, then Set the Connector on your device(s) - to send data from these devices to your endpoint.
Integration Documents Required:
For JSON HTTP integration you will require these 2 documents:
-
DMT JSON Device Integration: this describes how data is converted into JSON, and submitted to an endpoint with an HTTP POST.
- Integration Guide: Provides some context to the data fields and tips on the integration process.
4. Device Manager with the JSON MQTT connector
System Design
In this model, devices first connect to Device Manager, which then takes charge of sending any device data onwards through a Connector.

-
Device data: data is sent to Device Manager, and forwarded with a connector. Device Manager translates the device's native protocol into a JSON format and these records are sent to an endpoint over an MQTT connection. The connector specifies the topic, broker host, broker port and optionally a username and passord. Only secure MQTT over TCP is supported (mqtts://).
- Device management: all of the device management and debugging features are available through the Device Manager web user interface.
Device Manager cannot be bypassed in this setup, as the JSON MQTT conversion happens on Device Manager.
Many users prefer this option over the TCP option, as messages do not need to be parsed out of the TCP stream of bytes - which can be a learning curve for developers not used to writing TCP listeners. In contrast, many developers will be used to working with JSON - so it can be faster to integrate devices using this method.
To Get Started
Create a Connector in Device Manager, then Set the Connector on your device(s) - to send data from these devices to your endpoint.
Integration Documents Required:
For JSON MQTT integration you will require these 2 documents:
-
DMT JSON Device Integration: this describes how data is converted into JSON and submitted to an endpoint via an MQTT connection.
- Integration Guide: Provides some context to the data fields and tips on the integration process.
5. Device Gateway
System Design

Device Gateway is a lightweight, self-hosted integration option for customers who require devices to connect directly to their own infrastructure rather than Digital Matter cloud services.
It provides a secure, “air-gapped” device server that receives encrypted payloads from devices and exposes them via REST APIs for onward delivery to customer systems. Device Gateway is supplied as a packaged solution including a server component, API, and web-based user interface, and is deployed within the customer’s own environment (typically using Docker).
This option is intended for high-security or data-sovereignty deployments where devices must not connect to Device Manager. For most use cases, Digital Matter recommends using Device Manager, which offers a richer feature set, multiple connectors, automatic updates, and full support.
Device Gateway supports core device management functions such as device provisioning, firmware management, parameter templates, and asynchronous messaging, but requires key resources (device keys, templates, GNSS aiding data) to be manually exported from Device Manager and imported into the self-hosted environment.
6. Direct Integration (Raw TCP Payload to 3rd Party Server)
System Design
The final integration option bypasses Device Manager entirely and sends data direct from the device to a 3rd party server.
There is very little difference between the data received directly from a device and from the Device Manager TCP connector. Mainly, integrations via Device Manager will filter out device debug messages and many device profiling counters, whereas a direct integration will not.

When doing a direct to 3rd party integration, integrators are encouraged to start doing so via the Device Manager and a raw TCP connector. This provides much more diagnostic information and the full Device Manager suite of tools for removing variables when troubleshooting. Once this is working, the devices can be instructed to send directly to the 3rd party.
For managing firmware updates and parameter adjustments there are three main approaches:
-
Periodic Device Manager connection - Devices can be set up to periodically connect to Device Manager to check for configuration updates on a schedule. 🌟This is our recommended option when going direct.
- No other data is sent to Device Manager
- Devices can receive firmware and settings from Device Manager
- Devices are editable in the Device Manager Web UI
- The debugging and health check features of Device Manager are not available.
- The Web API can be used to remotely set up parameters that each device should update without using the Device Manager front-end (see below).
- No other data is sent to Device Manager
-
Check-in with Device Manager only on instruction - the devices will normally only connect to the 3rd party server. At the integrators discretion they can be instructed to connect to Device Manager with an async message (a downlink) to check in with Device Manager and take any queued updates. For example, this would be done when a settings update has been queued on Device Manager and the 3rd party server tells the device to go and fetch it.
-
Bypass Device Manager altogether - parameters can be configured via downlink. This is tantamount to developing your own bespoke device management platform. This should only be attempted under exceptional circumstances (e.g. security concerns). Contact your Digital Matter representative to arrange a support package if this is your only option.
Firmware-Over-The-Air (FOTA)
There is no capability to perform firmware updates Over the Air outside of Device Manager - the device must reconnect to Device Manager to update firmware. If you have the device in hand, a Wired Provisioning Tool can be used to manually update devices.
To Get Started
Setup instructions for integrating a raw TCP payload to a 3rd party platform can be found here: Setting up Direct to 3rd Party Server messaging on devices.
Proceed with Caution!
Device Manager provides several key functions (like GNSS aiding data downloads to devices) which are critical to device performance. See Direct to 3rd Party Server integration - Considerations to make sure you are aware of the implications of pursuing this approach.
Device Manager API
The Device Manager API provides a few features that enable some control of device configuration from a 3rd party platform.
Device Manager Actions
Key features:
- Set device admin and system parameters
- Get a list of parameter templates, and set them. This allows parameters to be changed programmatically to pre-defined templates. There is no option to set individual parameters.
- Set the Batch String in Device manager
- Change connectors
- Set enabled/disabled in Device Manager
Async messages
Async messages (downlinks) can be sent to the device. The Device Manager API can be used to queue the message on Device Manager which will then send the message to the device. Key messages are:
- Enable/disable Recovery Mode
- Set/unset digital outputs
- Turn immobilisation off/on
- Reset the device
The API opens up some useful functionality, as the device can be controlled programmatically based on other events happening. Examples include:
- Setting connectors/parameter templates when provisioning a device in a 3rd party front-end platform
- Changing parameters templates at certain times of the day (to adjust reporting rate)
- Allowing parameters to be controlled from a front-end UI
For more information and detailed documentation, please contact Digital Matter support.
Multi-Connector Integration
Data can be sent to multiple platforms simultaneously using a Multi-Connector (sometimes referred to as a 'splitter'). This is commonly used to send data to Telematics Guru and another platform.

Multi-Connector FAQs
What happens when one endpoint rejects the data but the other accepts it?
If you set a multiconnector, and one endpoint is rejecting the data, Device Manager will record it as a failed commit in the device grid.
Because the device doesn't receive a successful response from Device Manager, it will continue to upload the same records over and over until both connectors accept the data.
This means the one accepting the data will continually receive the same data.
You can view which connector is failing in the server logs:

In the above screenshot, Cam Test Connector is mean to send data to TG APAC02 and TG APAC03. The commit to APAC02 is failing.
Security and Encryption
A number of devices connect to Device Manager over an encrypted connection. The encryption is a CCM Mode block cipher scheme, using AES256 keys. Keys are shared securely between the device and server.
Encryption is device to Device Manager. After Device Manager, other measures are required, such as SSL. So if you require full end-to-end encryption, currently the best option is to use Device Manager and a HTTPS connector. Speak to Digital Matter to discuss your security requirements.
Next Steps
Your next step might be to set up your integration in Device Manager by creating a Connector. Once created, you will then need to set your Connector against your devices for it to function.
